These threats are designed to capture usernames, passwords, bank details, network information, and other sensitive data, says security provider Lastline.
Cybercriminals have been busy devising email campaigns that take advantage of the coronavirus outbreak. By promising information or help about the pandemic, these attacks instead infect unsuspecting recipients with malware, often designed to capture personal information. One such campaign analyzed by Lastline uses infostealers to obtain private data from its victims.
In a blog post published Monday, Lastline said that it’s detected a variety of threats centered around COVID-19, and many of these threats are infostealers. Some of the infostealers analyzed are older ones. For example, the Hawkeye infostealer has been active since around 2013.
Others are relatively fresh. The 404 Keylogger first appeared on a Russian dark web forum in August 2019, according to Lastline. Both of these threats use keylogging to record the keystrokes entered by the user to capture passwords and other typed information.
Whether relatively old or new, these email-based threats have been updated to exploit the coronavirus. All the email subjects contain at least one keyword related to the pandemic, such as “Coronavirus,” “COVID-19,” or “Corona.” The body text of the email uses urgent social engineering language about the disease. And the file attachments in these emails are given coronavirus-related names, such as “CENTER FOR DISEASE CONTROL_COVID_19 WHO DOCUMENT_PDF” and “Letter_to_customers_covid-19_pdf.”
By using keyloggers, many infostealers try to to steal such information as usernames, passwords, and banking data. Some infostealers, such as Agent Tesla, have evolved into more advanced threats able to steal Wi-Fi passwords. Some, such as Trickbot, are capable of capturing system and network information. And some, including Trickbot and Hawkeye, can even grab the contents of cryptocurrency wallets.
Analyzing the activity of infostealers during March 2020, Lastline found that different threats were active on different dates. On March 2, both Lokibot and Trickbot campaigns were in force. A week later on March 9, Lokibot was again detected. The following day on March 10, Lastline found active campaigns using Hawkeye. On March 24, the 404 Keylogger dominated the daily charts.
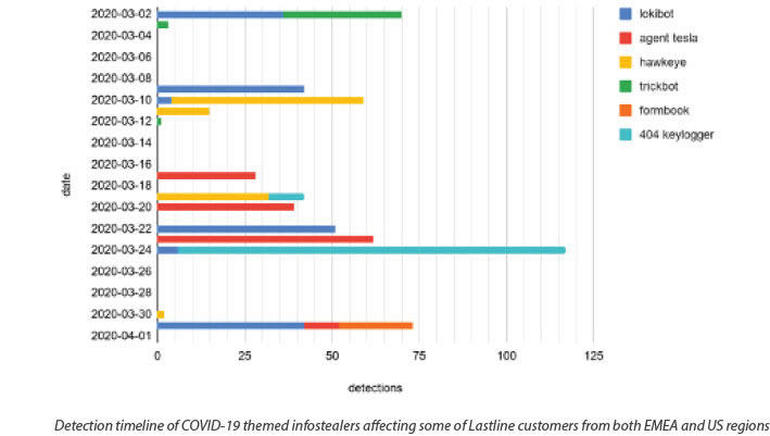
Most of these campaigns rev up during the week, starting with Monday, and then slow down over the weekend. Spammers and malware operators specifically target people who are back on the job on Mondays, even as they work from home. There’s little point launching an attack on a Saturday when people aren’t working and when security personnel and products can respond to that attack before it hits users on Monday.
The threats also vary based on region. In the EMEA (Europe, Middle East, Africa), the most common and persistent infostealer seen by Lastline in March was Lokibot. The popularity of Lokibot may be attributed to the 2015 leak of the original source code, which triggered many variants and recompiled editions deployed by different cybercriminals.
In the US, no one single infostealer has dominated the attack pattern. As the US is a large market with a single language, cybercriminals seemingly tend to deploy all types of attacks, from unsophisticated keyloggers to multi-stage stealers, according to Lastline.
Finally, most of the infostealers detected use a “Malware as a Service” model and are sold at affordable prices on the dark web. The main factor that distinguishes one campaign from another is the configuration rather than the code. Cybercriminals simply redesign existing email campaigns to take advantage of new areas, such as the coronavirus.



